Introduction:
In today’s technology-driven world, it's almost impossible to imagine life without mobile apps and the internet. We all rely on mobile apps for our day-to-day tasks such as paying bills, ordering, shopping, and much more. Giving such comfort and accessibility, it has made our human life so much easier but as everything has its dark side, this too comes with some cons.
Today almost every app collects data, access permissions, and whatnot. This means your data is not private anywhere and is somewhere stored on Google, and if it's exposed to the wrong person, it can turn out into a cyberattack. According to Forbes, 94% of businesses reported about email cyber incidents.
Over 34% of malware are sent via email because hacking email means access to every business and personal details. It's important to use mobile apps smartly and watch where you are sharing your data.
In this article, we are gonna discuss cyberattacks, best practices to keep your mobile app secure, and many other useful things.
Let's move further.
What is Mobile Application Security?
Mobile app security is about securing sensitive information on mobile devices from cyber threats. It includes using encryption, authentication, and secure data storage to make sure it is only used by authorized users.
Why Mobile Application Security is Important?
Data leaks can result in life-threatening conditions if they get into the wrong hands. You can expect worst-case scenarios if a mobile app is hacked hence mobile app security is very important due to the following reasons.
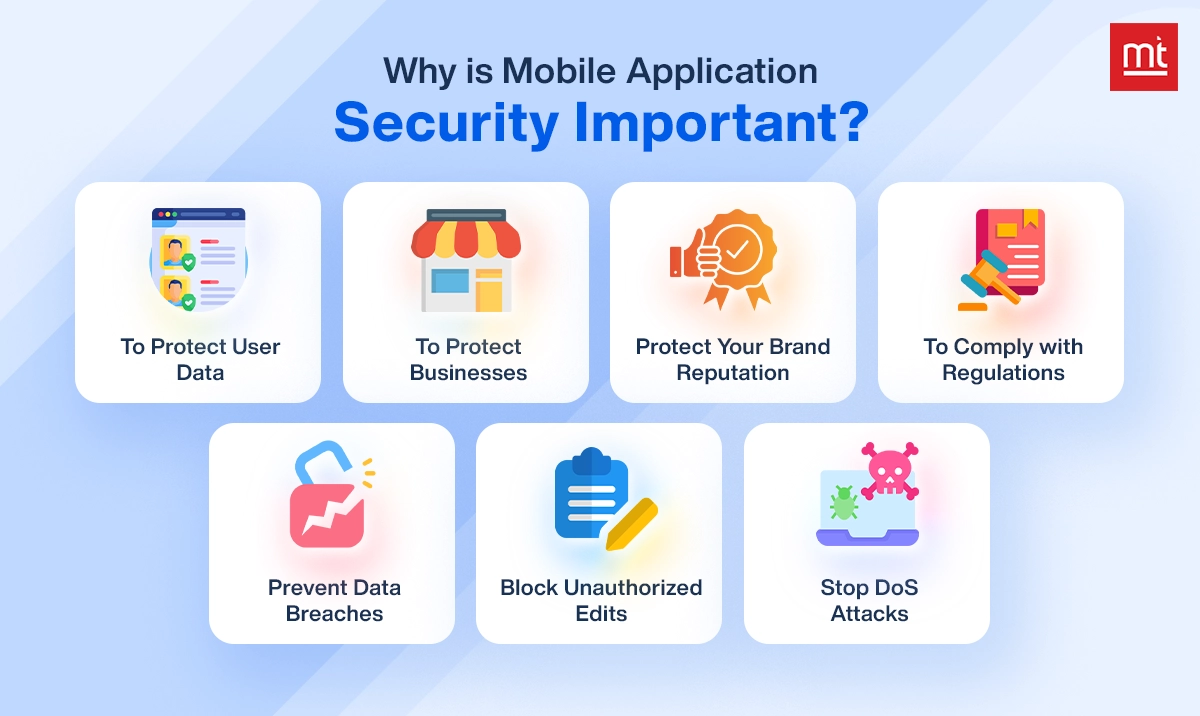
1. To Protect User Data
Whenever you install any app, it first asks you to log in or sign up using your email or contact number. These might seem like basic details but it can be misused in any way if you have the same number or email ID in your bank. Mobile app security helps to verify and protect users from identity theft, fraud, or privacy violations.
2. To Protect Businesses
It is important to maintain the credibility and trust of the business. If you have moved your business to online on mobile apps, data security is a must to prevent financial losses.
3. To Protect the Reputation of Organizations
Even a single data breach can ruin your decades of business and hard-earned image. Hence always prioritize user safety to maintain a loyal customer base and ensure a good reputation for your business app.
4. To Comply with Regulations
It also shows that you follow all legal laws and compliance, adding worthiness and credibility to your business. It also protects you from unexpected fines and legal consequences.
5. To Prevent Unauthorized Access to Sensitive Data
Robust app security helps to protect customer and business data such as your strategies and other confidential information.
6. To Prevent Unauthorized Modifications to Data
The security of mobile apps prohibits unauthorized access by hackers to alter data and its accuracy and reliability are maintained. This is crucial if your app involves money transactions, medical records, or sensitive business engagements.
7. To Prevent Denial-of-service Attacks
DDOS attack directly affects the functionality of all. This works by making the functionality unavailable to users. Hence always follow security measures to mitigate these attacks to make sure your business app works optimally for the users.
Challenges in Mobile App Security
Every business is differently designed and developed and so they have different security concerns too. This makes it challenging to fulfill mobile app security. Let's have a look at some of the challenges below.
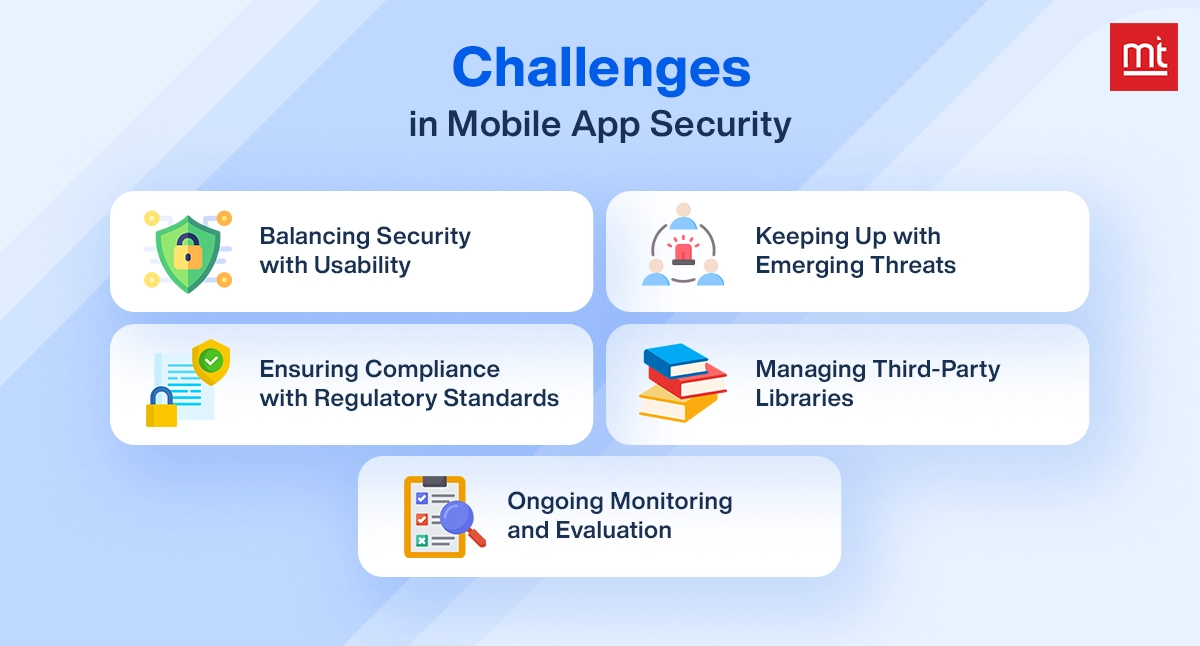
1. Balancing Security with Usability
It becomes hectic to balance both security and usability because if we logically see, some apps might require multiple authentication steps that can be time-consuming for users.
2. Keeping Up with Emerging Threats
As technology evolves, so do cyber threats too. Day by day, cybercriminals are getting new ideas for extorting data and hacking. Hence it is the responsibility of developers to always make room for improvement for updating app security and stay updated with the latest threats in the market.
3. Ensuring Compliance with Regulatory Standards
Different regions and industries have specific data protection laws like GDPR or HIPAA. It's important to meet compliance with legal standards if your app is used across the globe or targets specific regions.
4. Managing Third-Party Libraries
These days, developers often use third-party libraries in the app code. This might come with some glitches and might not be safe to use. So, always check and verify the external codes or libraries to ensure they perform best inside the app.
5. Ongoing Monitoring and Evaluation
Mobile app is not a one-time task that you launch and it's done. It's a life-long investment so you must do regular maintenance, evaluate it, run a security check, and read user reviews to know if there is any issue with the app's performance.
Mobile App Security Checklist: How to Secure Mobile Apps?
You can prevent cyber threats and fraud if you follow the right checklist. Below we have made a well-researched mobile app security checklist that is worth trying out.
1. Secure Coding Practices
Trouble begins with the poor code. Code is the base of mobile applications, if the code is robust, clean, and written using safe methods, it can prevent vulnerabilities from entering at the first stage. This includes input validation, authentication, data encryption, etc.
2. Authentication and Authorization
Implement robust authentication and authorization methods in the code so that it's impossible to access outsiders. Use suitable permissions, user roles, and multi-factor authentication so that it's easy to prove user identity.
3. Data Encryption and Protection
Always use secure protocols like HTTPS for data transmission and strong encryption algorithms to keep user information safe. Use data encryption to make data invisible to users.
4. Prioritise API Security
API is responsible for linking applications with different servers and services, and it can act as an entry point for cybercriminals to enter the app. To secure these important paths, make use of authentication tokens, encryption of API communication as well as data exposure limitation.
5. Penetration Testing and Vulnerability Scans
Penetration testing (or in short pen test) is an attempt to try a real-life cyber-attack where experts try to gain unauthorized access to a system with the intent of discovering its weaknesses. It's like doing rehearsal and acting like cybercriminals to know the possibilities of the threats.
On the other hand, a vulnerability scan is an automated tool that identifies, reports, and scores known vulnerabilities in computer security without actually probing the network or system for weaknesses.
Pro tip: Invest in mobile app security testing as it helps to future-proof the app from threats and other issues.
6. Runtime Protection and RASP
Implement runtime protection and RASP tools to actively monitor the app and catch vulnerabilities in real-time.
RASP is basically software that can be embedded within the app to catch the threats and block them.
7. Secure Data Storage
Data storage is an important concern. Use data segregation and secure containers to store the data safely. Data segregation includes storing the data into different sets in different databases. This reduces further access during the breach which limits the extent of the damage.
On the other side, docker containers and all come under secure containers where the app data is isolated from other data, creating a protective wall.
8. Logging and Monitoring
Implement centralized logging systems to record every detail of the application, user activities, and system crashes. This in turn helps the data security team to interpret the data and identify any anomalies.
Use real-time Monitoring to keep track of these logs and events constantly, detecting threats in real-time. This helps to act fast in case of counterattacks and prevent damage.
9. Patch Management and Compliance
Make sure your mobile app is updated with the latest patches. A good patch management strategy is important to address the vulnerabilities before the attackers take advantage of them.
Also, routine monitoring of apps is compulsory so that you don't have to face legal liability issues in the future.
10. Code Obfuscation and White-Box Cryptography
Hackers are obviously coders and technical people, so what you can do is code Obfuscation which means write code in such a twisted way that it's hard to understand for them. It includes changing logic, code structure, and more.
White box cryptography is a method of securely embedding keys securely in the app without exposing it.
Emerging Patterns: Trends in Cyberattacks and Cyber Threats
1. Ransomware on the Rise
Ransomware attacks are on the rise because of increasing remote work. It is a type of malware or virus that is sent to the victim’s pc which locks the system. What the criminal do is hack important business data and ask for payment to release their data. It's actually like blackmailing someone for money. This happens most commonly to big organization and business.
It is possible to tackle ransomware attacks by protecting systems with regular backups, robust security measures, and employee training to reduce potential damage.
2. Internet of Things (IoT) Vulnerabilities
Many devices used in the Internet of Things such as smart home devices or connected medical devices do not have strong security protocols in place. This presents an opportunity for hackers to infiltrate these networks or harvest sensitive information. As the adoption of IoT technology continues to grow, it is very important to make these endpoints secure through encryption, periodic updates, and secure access mechanisms to prevent unauthorized access to the systems.
3. Social Engineering Attacks
You might have seen many websites or apps asking for money, manipulating you by gaining your sympathy, this technique is social engineering.
Fraudsters try to get sensitive information using phishing emails or pretext calls. This type of attack is focused on the person's action rather than a compromise in technology. This can be prevented by educating workers with the skills to identify social engineering attacks.
4. Supply Chain Attacks
It is common for hackers to gain entry into systems by exploiting weaknesses in third-party vendors or supply chain partners. By manipulating a vendor, it becomes easier for them to obtain the information held by an organization. As the supply chain gets more intricate, it becomes even more important that all the partners involved adhere to inflexible security measures, especially with regard to sensitive data, in order to avoid any form of security compromise.
Key Takeaways for Building a Secure Mobile Future
It's better to be aware and smart rather than being sorry later. Hope this blog helped you learn about useful practices and cyber attacks. You can only protect your organization if you have the right knowledge about the cyber attacks and mobile app security.
Mobile app security is crucial and a continuous on-going process hence it requires constant monitoring and upgrading of security terms and policies. Most importantly, always get this done by experienced and skilled developers on whom you can rely for mobile app security.
How ManekTech Can Help?
At ManekTech, we don’t just develop mobile applications – instead, we build secure digital experiences. As a reputed mobile app development company in the USA, our proficient developers make sure your application is not only creative but also protected to the maximum extent.
Now let’s make your idea a reality while also ensuring the safety of your users and their information. Send us a message and let’s get a free estimate to develop an innovative and secure mobile solution for you that will give you the best of both worlds – creativity and safety.
Make dedicated developers available now – your application is worth that and more!
About Author
Subscribe to Our Newsletter!
Join us to stay updated with our latest blog updates, marketing tips, service tips, trends, news and announcements!


![How Much Does It Cost to Build a Mobile App? [Checklist]](https://www.manektech.com/storage/blog/image/1708005911.webp)